Cloud storage has revolutionized data storage in various aspects. Firstly, it is possible to access data from any location or device. Then, it has made file-sharing easier than ever before.
There is no doubt cloud storage is the future. But with these extraordinary benefits, you are also exposed to cloud threat. In this article, we are going to discuss everything you need to know about cloud security threats. We will discuss some common security threats in cloud services, ways to overcome them, and a robust cloud security strategy.

What are Some Cloud Security Threats?
Cloud storage is exposed to a wide range of threats because of its online availability. Out of those, here are some of the major ones.
Unknown Access
It’s the responsibility of the cloud storage to offer access to the right persons, the owner of the account, and prevent unknown and unauthorized access.
Attackers try to access users’ accounts. They guess the password and take other information through social media. Once the password is guessed or cracked, they gain access to the account.
They can do anything with the data stored in the cloud storage and harm the owner. It is essential for cloud storage services to tackle this issue to ensure the security of their users.
Data Breach
Data breach is another issue with cloud storage.
Hackers can get access to your data during its transport from one device to another or sharing. They could also get access to your account, private data, confidential files, etc.
Once hackers get your data, they can blackmail you, share it with the public, ask for money, etc. In such cases, your data is always at risk.
Hackers can also sell your personal data to third parties.
Insider Threats
If you go with unreliable and non-trusted cloud service providers, you are exposed to insider cloud security threats.
For instance, if the service provider does not have strict and advanced in-house security, the workers could access your private data.
There are chances of data leakage, and service providers can even sell your personal information, such as email.
When you aren’t sure about the data security measures inside the facility or at data centers, it is better to avoid such cloud service providers.
Malware Attacks
Cloud storage is also susceptible to malware attacks.
Attackers can inject malware into the storage, which can also be transferred to the applications and synced devices. It can disrupt the operation of the cloud storage. It might not allow you to access the data or delete it. They can also steal your data through malware.

How to Overcome Cloud Threats?
Cloud storage is definitely exposed to multiple threats, but these can be overcome through robust solutions. Let’s see how service providers tackle cloud based security threats.
The issue of unauthorized access is resolved through multiple layers of security and best practices. Users are requested to create difficult passwords that aren’t easy to guess. Therefore, it becomes difficult for attackers to access the account. Secondly, cloud service providers offer two-factor authentication (2FA). It requires two forms of identification, which could be a password and code sent to the connected smartphone. It prevents unauthorized access.

Once 2FA is applied, the chances of a data breach are mitigated. To further reduce the changes, the data is end-to-end encrypted. It means only the user can access data or the receiver. There is no way others can access it. Even if the data is accessed, it can be decrypted. Moreover, service providers monitor the activities on the account. If the account is accessed from a new or suspicious location or device, the account owner is alerted through a notification.
Insider threats are prevented through tight internal security at the data centers. Secondly, cloud encryption ensures that not even the workers of the cloud storage can access your data.
Malware attacks are vulnerable. Therefore, cloud service providers take multiple preventive measures to deal with this cloud threat. Firstly, the network has multiple layers of security, such as a firewall and anti-malware software. These prevent malware attacks.
Secondly, there is a team to monitor these cloud security threats. The cloud storage is scanned regularly to look for malware and weaknesses. It alerts teams about any issue. Nowadays, service providers use machine learning algorithms to detect malware attacks. Then, they respond immediately.
What Does a Robust Cloud Security Strategy Include?
A robust cloud storage security includes the following aspects.
Reliable Data Centers: The data of cloud storage should be stored in countries that care about users’ privacy. There should be privacy laws to govern the use and access of data. The service providers need to pick reliable locations where the data remains safe.
User Education: The users of the cloud must be educated about strong passwords, sharing security, end-to-end encryption, how to report a security threat, etc. The service provider must educate users through blog posts, videos, social media, etc.
Authorized Access: Service providers need to implement strong passwords that include upper case, lower case, and special characters. They need to enable Two-factor Authentication (2FA) or Multi-factor Authentication (MFA). They should have a robust identity management system to allow access only to the right person.
AI Detection: Implementation of AI detection is essential nowadays. It scans massive storage space and identifies a cloud threat quickly. It makes the storage more secure. Service providers need to invest in machine learning to compete with other reliable competitors.
Encryption: Encryption is a must for cloud storage. It prevents data breaches and makes cloud storage a secure option. Service providers need to adopt advanced encryption algorithms that are almost impossible to decrypt. Everything on the cloud must be end-to-end encrypted.
Threat Prevention: Preventive measures, such as firewalls and anti-malware, must be adopted to prevent cloud threats. They keep an eye on suspicious activities and make the storage secure.
Data Recovery: There should be backups and data recovery solutions. In the case of any problem, the data of the users must be safe.
Response Team: A dedicated team is required to deal with customer issues, cloud threat, malware, etc. They should be ready to monitor issues and take immediate action.
Choosing a reliable and secure cloud storage is a challenge. You have to consider multiple factors and ensure the storage is safe from cloud threats. There are tons of options available, but choosing a secure option is extremely difficult.
TeraBox is secure cloud storage that users can use without any worries. It implements a robust strategy to ensure the data of users is secure.
Firstly, TeraBox is encrypted. The data stored in the storage is end-to-end encrypted, which means not even the workers of TeraBox can access it. Its server-side encryption is exceptional. There is also a special space called Safe. It protects your data with an additional password. So, even if someone gets access to your account, the data inside the safe will be inaccessible.
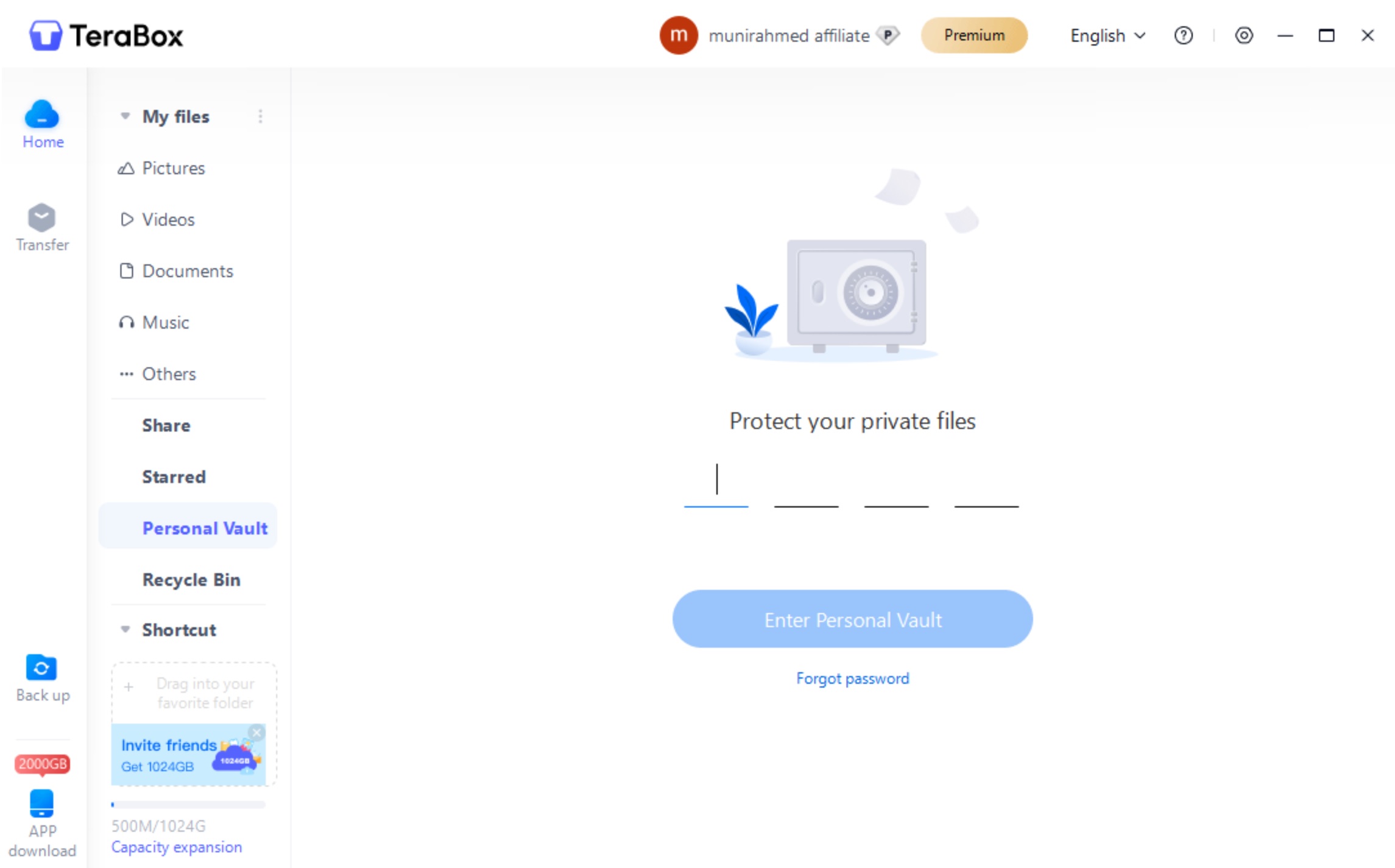
It also has transport layer encryption, including SSL and TLS, to keep your uploads, downloads, and sharing safe. The data cannot be ready by hackers or any third party. You also have control over your shared files. You can set a password, restrict users, and even set a validity period for the link.
TeraBox implements two-factor authentication (2FA). Users can enable it from the application and make their accounts more secure. It’s an extra layer of identity verification. There is no way anyone else can access your account. Even TeraBox’s team monitors account access and tackles potential threats in cloud.
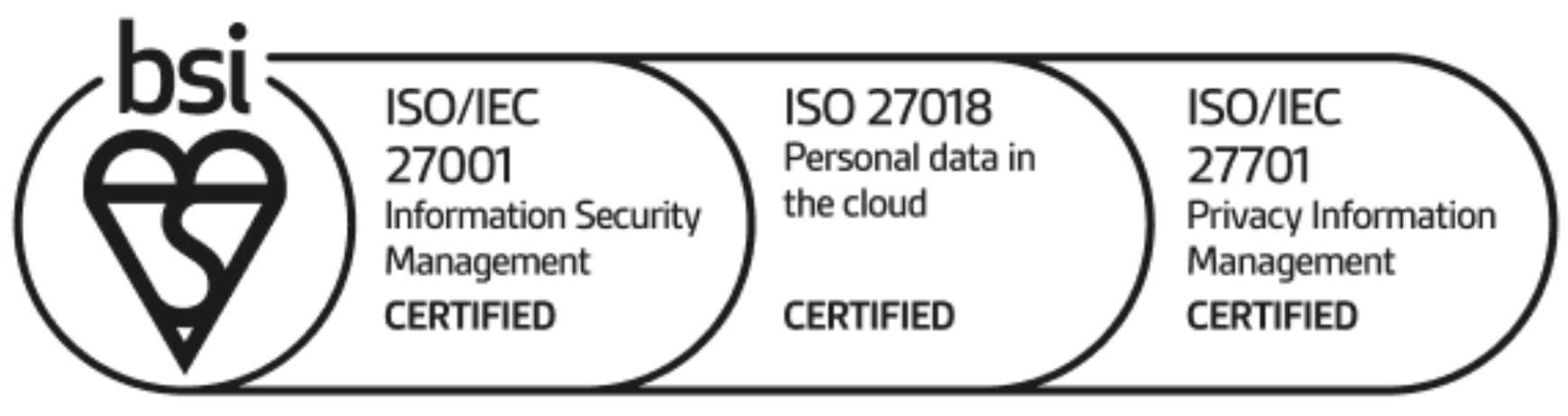
Most importantly, TeraBox cares about your privacy. It follows international security and privacy standards. It currently holds three global certifications, including ISO 27001, ISO 27701, and ISO 27018.
Even after cutting-edge technology and tight security measures, TeraBox offers up to 1TB of free storage to its users. They store their data from multiple devices and access it from any location.
Further reading: Is TeraBox Safe and Secure?
Final Thoughts
Cloud storage is susceptible to various cloud security threats, but overcoming them is the duty of the service provider. It is necessary to ensure the users’ data is safe and secure. It should prevent unauthorized access, data breaches, malware attacks, and other cloud threats.
We have discussed all these in detail and how to overcome them to make cloud storage more secure. If you are looking for reliable and secure cloud storage without a cloud threat, TeraBox is an excellent choice. It offers up to 1TB of free storage, robust security, exceptional privacy, and advanced features. Download TeraBox APK and use it without any worries.